Corporate governance Corporate governance
- Information and communication security risk management framework:
(1) The IT department is responsible for developing policies, plans, measures and technical regulations related to information and communication security, and for matters related to the research, deployment and evaluation of security technologies.
(2) The relevant business department is responsible for matters concerning the development of security requirements, management of use, and maintenance of data and information and communication systems.
(3) All employees and contracted service providers are required to follow the procedures for security management to maintain the information and communication security policy.
- Information and communication security policy:
(1) Purposes:
This policy has been established to maintain the overall information and communication security of the host, network equipment and network communications of the Company, effectively mitigate the risks of theft, unfair use, disclosure, alteration, service suspension or destruction of information assets due to negligence, intention or natural disasters, ensure the confidentiality, availability and integrity of such assets, and meet the Company’s need for normal operations.
(2) Goals:
- To create a secure and reliable information and communication environment by strengthening the management of information and communication security and enhancing the capability for protection.
- Confidentiality: Making sure any information in the information system during processing or transmission is accessed by the right person, at the right time, on the right device and in the right place to ensure the information system is accessible only to authorized persons and to protect confidential data from leaking.
- Integrity: Any data stored in the Company’s information system must be protected during processing or transmission to prevent improper alteration and improper manipulation or breach of the information system during its operation.
- Availability: Ensuring that any authorized user is able to receive a response and complete the required service within the appropriate time whenever the user needs to use the information system.
- To ensure the availability of core services and network operations.
- To ensure that services interrupted by system failure as a result of any information/communication security incident or other anomaly is able to return to normal operation quickly.
- To ensure the Company’s information and communication security measures or regulations meet the requirements of applicable laws and regulations.
- To ensure that any information/communication security incident or suspicious vulnerability is reported through an appropriate reporting mechanism and properly investigated and addressed.
- Concrete management programs, and investments in resources for cyber security:
The Company establishes the safe information environment and continue to invest the fund to improve vulnerability and upgrade the system’s performance. The main cyber security management programs are stated as follows:
Network security | Construct the network firewall to block external cyber attacks Construct the endpoint protection to stop computer virus and hackers’ invasion Construct the mail backup anti-virus mechanism to block spam attacks and satisfy the SOX Act to track the search record |
Information system security | Construct the data backup mechanism to back up the data in the important system and practice the backup exercise periodically Virtualize important application systems and produce backup thereof on a daily basis |
Application security | Establish the application system development process in accordance with SOP for application, testing, acceptance and inspection & acceptance Information system outsourcing maintenance controlled by remote access following information security authority control |
Education & training and promotion | Periodic information security promotion and education & training Strengthen employees’ awareness toward email social engineering and execute phishing email exercise |
Employee information security | Execution of the NDA for employee security Provide employees with the on-the-job education and training to ensure the safety and accuracy of various information assets and operating systems. |
The Company’s cyber security reporting procedures are defined as follows. Any information security incident shall be reported and processed in accordance with the procedures.
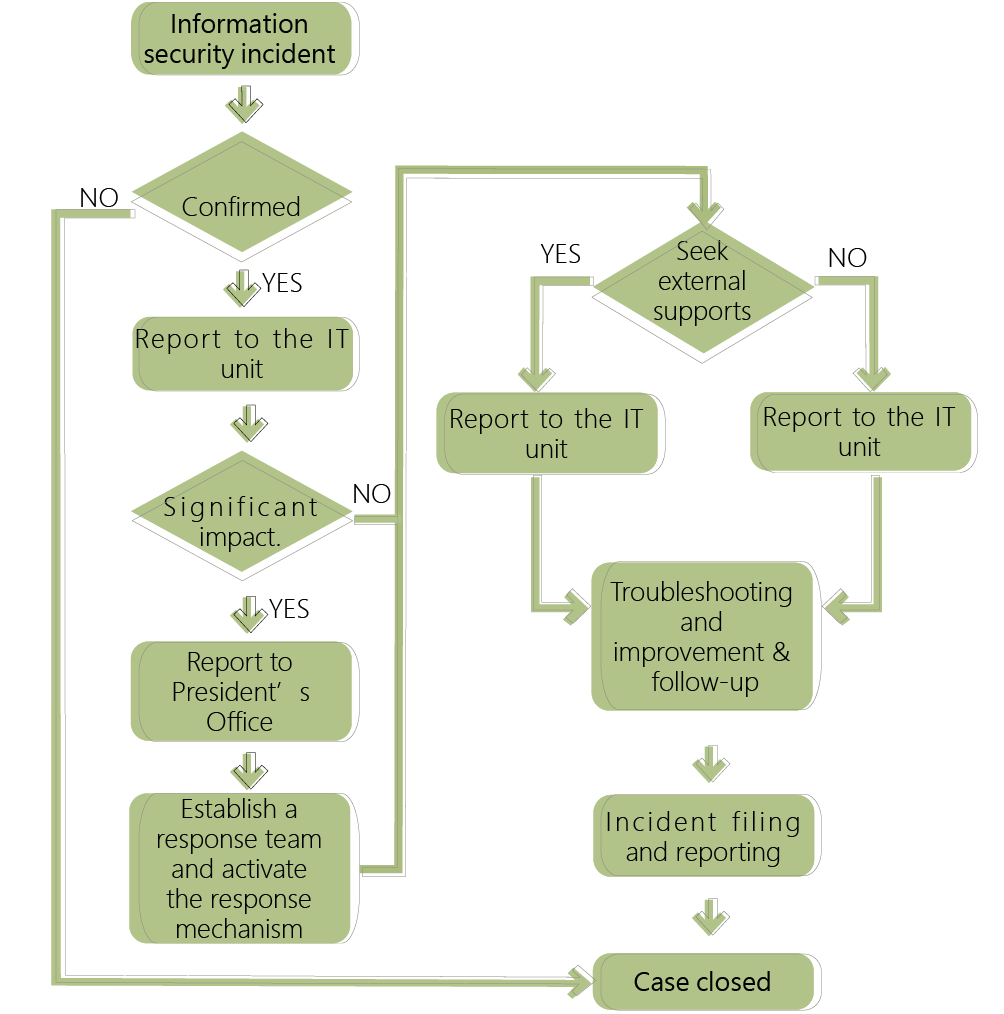
Everyone should be responsible for information security. No matter how strict the security of a system is, without the users putting the concept into action, it is still impossible to minimize the risks. Therefore, after the occurrence of each abnormal event, the Company not only records the entire process of the event but also prepares announcement thereof to inform all employees so that every employee may have more understanding of information security protection and implement it accordingly. By this continuous circle, every employee may be more aware of the information security during operation to strengthen the security of information, reduce threats and improve the Company’s competitiveness. The Company accepts an audit of internal control every year to verify the level of information security risk. If relevant standards are not met, the Company will take improvement measures to mitigate possible risks. Since the audit of internal control in December 2022, there has been no risk event of a significant information security incident affecting business operations.
As of the date of publication of the annual report, the Company has not discovered any significant web attack or incident that has or may have caused significant adverse effect on the business and operation of the Company. Also, the Company has not been involved in any related legal actions or subject to any related monitoring and investigation.
According to the Guidelines for Establishing Internal Control Systems for Publicly Issued Companies, on October 31, 2023, one Information Security Manager and one Information Security Officer were appointed. Manager Liu Weinan serves as the Information Security Manager, and Deputy Section Chief Lai Jianming serves as the Information Security Officer. They are responsible for planning, monitoring, and executing information security management operations.

